Penetration testing often fails before the first test case is written or the first packet is sent. Not because the systems are complex, nor because the attacks are particularly advanced.
The real issue is unclear language.
Terms like pentest, vulnerability scan, red team, and PTaaS are frequently used interchangeably, even though they represent very different activities, outcomes, and levels of business risk.
When language is unclear, teams approve the wrong tests, interpret results incorrectly, and walk away with a false sense of security. In high-risk environments, especially Web3, those misunderstandings can become extremely expensive.
At Zokyo, we see this disconnect repeatedly. This guide exists to fix that.
The goal is to ensure that when a security test is approved, a report is reviewed, or a vendor is evaluated, everyone understands what is actually being tested and why it matters to the business.
Why Penetration Testing Terminology Gets Confusing
Penetration testing is complex, living at the intersection of engineering, risk management, compliance, and commercial delivery. Each group uses the same terms but often meaning different things.
- Security engineers think in terms of exploitability and attack paths
- Executives think in terms of business impact and risk acceptance
- Vendors often describe scope and delivery models
Without shared definitions, teams cannot be aligned. Miscommunication produces the same failures again and again:
- A vulnerability scan is approved when leadership expects attacker simulation
- A red team is requested when basic exposure testing would have delivered more value
- A "pentest report" is delivered that lists issues, but answers none of the underlying business questions
Clarity in language is the foundation of effective security. That's why we also have a full guide on the art of writing security reports.
Core Concepts Every Decision-Maker Should Understand
Penetration Testing (Pentest)
A penetration test is an authorized, controlled attempt to simulate real-world attacks against systems, applications, or infrastructure.
Unlike automated tools, a pentest is driven by humans who actively: chain weaknesses together, bypass controls, and/or demonstrate real impact.
In essence, penetration testing explores what can realistically be abused and how far an attacker could go.
Vulnerability vs Exploit
This distinction is critical. A vulnerability is a weakness: a misconfiguration, logic flaw, or missing control. The exploit, on the other hand, is the technique used to abuse that weakness.
Most environments contain thousands of vulnerabilities, but only a fraction of them can be meaningfully exploited.
Attack Surface
Your attack surface is every possible way an attacker could interact with your environment. This includes:
- Public applications and APIs
- VPNs and authentication portals
- Cloud configurations
- User roles and access paths
- Sometimes even physical or operational exposure
As systems scale, attack surfaces grow. Penetration testing helps identify which exposure points actually matter.
Scope
Scope defines what is being tested.
It specifies the exact contracts, components, environments, and features under review. It also includes any constraints on testing methods, timelines, or system access.
Which Test Answers Which Business Question?
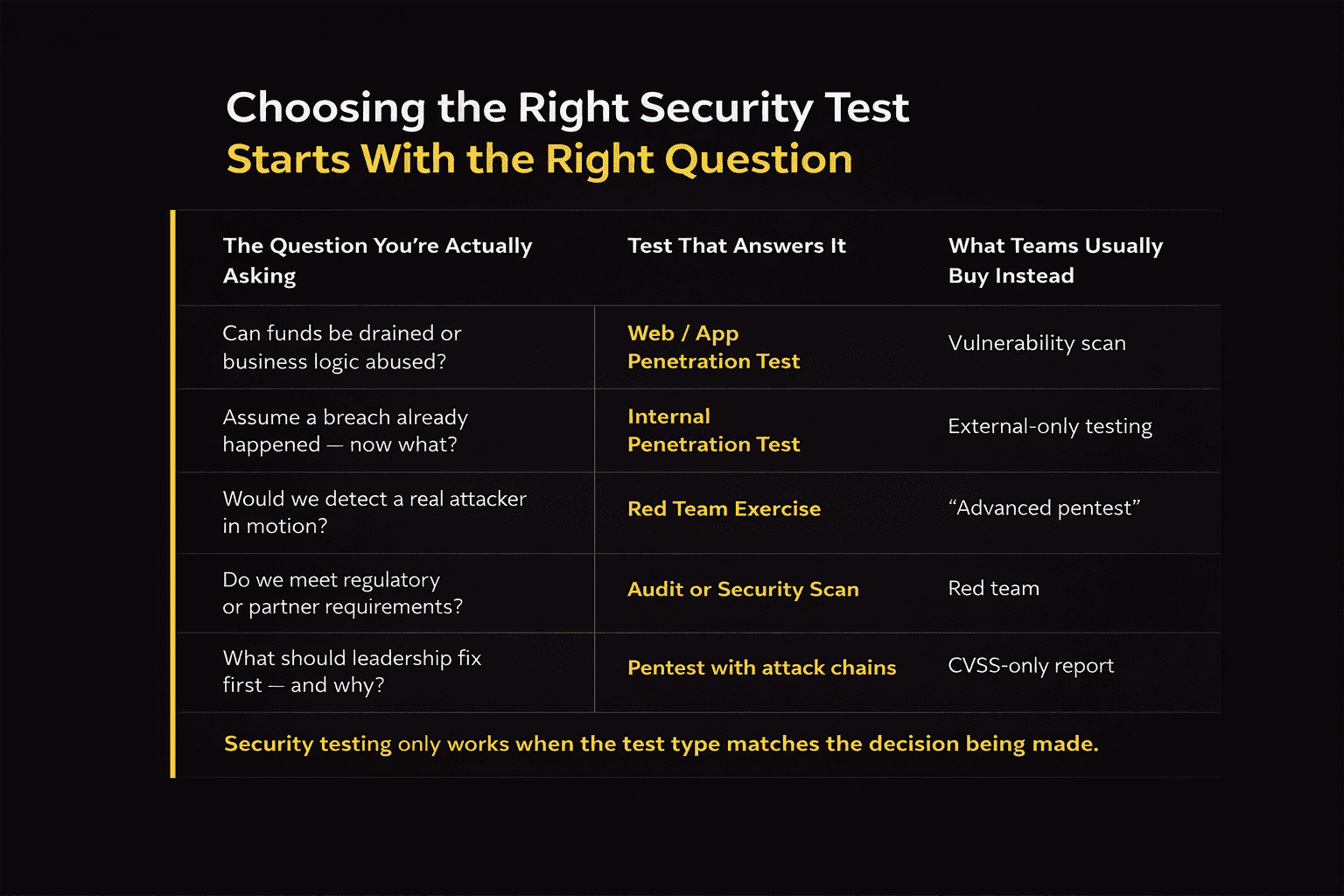
Comparison of testing methodologies and the business questions they answer
Common Types of Penetration Testing
External Network Testing
Simulates an attacker with no internal access attempting to compromise internet-facing assets.
Business question: If someone attacks us from the internet, what can they exploit?
Internal Network Testing
Assumes a breach has already occurred, often via a compromised device or account.
Business question: How far can an attacker move after gaining internal access?
Web Application Testing
Focuses on application logic, authentication, authorization, and data handling. For SaaS platforms, fintech, and Web3 applications, this is often where direct financial and user risk lives.
API Security Testing
Examines backend APIs used by mobile apps, partners, or internal systems. APIs often expose powerful functionality with less visibility and fewer controls than traditional interfaces.
Mobile Application Testing
Assesses mobile apps alongside their backend services, encryption, and local storage behavior.
Wireless Testing
Evaluates Wi-Fi networks for weak encryption, poor segmentation, or unauthorized access paths into internal environments.
Red Team Exercises
A red team engagement simulates a persistent, motivated attacker using multiple vectors, sometimes including social engineering or physical access. The objective is not just compromise, but to evaluate detection, response, and decision-making under pressure.
Understanding "Box" Testing Models
- Black Box: No prior knowledge. High realism, limited depth.
- White Box: Full internal knowledge. Maximum coverage and depth.
- Gray Box: Partial access. Most practical for modern organizations.
Each model trades realism for coverage. Choosing the right one depends on your threat assumptions.
Services Commonly Mistaken for Penetration Testing
Vulnerability Scanning
Uses automated tools to detect known vulnerabilities across systems at scale. They help maintain security hygiene, but do not model how vulnerabilities chain together in real attacks.
Authenticated vs Unauthenticated Scans
- Authenticated scans see deeper into systems
- Unauthenticated scans view the environment from the outside
Neither replaces human-driven testing.
Penetration Testing as a Service (PTaaS)
A delivery model, not a type of testing. PTaaS changes how tests are scheduled and consumed, not what penetration testing fundamentally is.
Why Web3 Penetration Testing Is Different
Web3 systems introduce risk characteristics that traditional models often miss:
- Immutable deployments: No hotfixes after exploit
- Economic attacks: Profit-driven abuse, not curiosity
- Composability: Your security depends on other protocols
- Privileged roles: Admin keys and governance often matter more than bugs
- Capitalized attackers: Adversaries deploy capital, not scripts
Effective Web3 testing requires threat modeling that goes well beyond code scanning.
How Risk Is Communicated in Reports
CVSS Scores
Numeric technical severity scores. They are helpful for engineers but insufficient for business decisions on their own.
Risk Ratings
Most mature reports translate findings into Critical / High / Medium / Low to support prioritization.
Ratings are typically based on impact, exploitability, exposure, and the potential blast radius of a successful attack. They answer a simple question: what should be fixed first, and why?
Attack Chains
Attack chains show how multiple low- or medium-risk issues can be chained together to achieve real compromise, often revealing risk invisible at the individual finding level.
Common Red Flags When Buying a Pentest
- No threat model discussion
- No attack chains
- Everything rated "Medium"
- Tool output disguised as analysis
- No business impact narrative
These are signals that expectations were never aligned.
Closing Thoughts
Penetration testing fails far more often due to misaligned expectations than technical shortcomings.
When teams use the same terms to mean different things, or different terms for the same activity, risk is misunderstood and resources are misallocated.
At Zokyo, we believe clear definitions, honest threat modeling, and actionable reporting are what turn security testing into real security outcomes.